Getting Linux to authenticate via LDAP
Eg:
Server: server.shirish.com (192.168.8.10)
Client : client.shirish.com (192.168.8.20)
Prerequisite :
Required Packages to be installed .
openldap
openldap-clients
openldap-devel
openldap-servers
nss_ldap
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/nis.schema
include /etc/openldap/schema/redhat/autofs.schema
allow bind_v2
pidfile /var/run/openldap/slapd.pid
argsfile /var/run/openldap/slapd.args
database bdb
suffix "dc=shirishlinux,dc=com"
rootdn "cn=admin,dc=shirishlinux,dc=com"
password-hash {CRYPT}
rootpw {SSHA}p+IMM8pNWzGirnHTizlpc2IwSrc6rgXR
Take backup of this script .
[root@server1 migration]# cp -rp migrate_common.ph migrate_common.ph_back
This script is made for domain "padl.com" which now we have to change for our "shirishlinux.com" domain as below before running this script .
[root@server1 migration]# grep -i padl migrate_common.ph
$DEFAULT_MAIL_DOMAIN = "padl.com";
$DEFAULT_BASE = "dc=padl,dc=com";
#define(`confLDAP_DEFAULT_SPEC',`-h "ldap.padl.com"')dnl
# $DEFAULT_MAIL_HOST = "mail.padl.com";
[root@server1 migration]#
We will do this changes by sed, but you can do by opening file via "vi" editor too .
First check :
[root@server1 migration]# sed "s/padl/shirishlinux/g" migrate_common.ph | grep -i shirish
$DEFAULT_MAIL_DOMAIN = "shirishlinux.com";
$DEFAULT_BASE = "dc=shirishlinux,dc=com";
#define(`confLDAP_DEFAULT_SPEC',`-h "ldap.shirishlinux.com"')dnl
# $DEFAULT_MAIL_HOST = "mail.shirishlinux.com";
[root@server1 migration]#
Above seems okay, now will implement changes using sed as below .
[root@server1 migration]# sed -i "s/padl/shirishlinux/g" migrate_common.ph
Verify Now ....
[root@server1 migration]# grep -i shirishlinux migrate_common.ph
$DEFAULT_MAIL_DOMAIN = "shirishlinux.com";
$DEFAULT_BASE = "dc=shirishlinux,dc=com";
#define(`confLDAP_DEFAULT_SPEC',`-h "ldap.shirishlinux.com"')dnl
# $DEFAULT_MAIL_HOST = "mail.shirishlinux.com";
[root@server1 migration]#
Similarly we will do for group file entry as below of the user "ldapuser"
[root@server1 migration]# grep -i ldapuser /etc/group > /root/LDAP/ldapuser_g
[root@server1 migration]# cat /root/LDAP/ldapuser_g
ldapuser:x:506:
[root@server1 migration]#
[root@server1 migration]# /usr/share/openldap/migration/migrate_group.pl /root/LDAP/ldapuser_g /root/LDAP/ldapuser_g.ldif
[root@server1 migration]#
[root@server1 migration]# cat /root/LDAP/ldapuser_g.ldif
dn: cn=ldapuser,ou=Group,dc=shirishlinux,dc=com
objectClass: posixGroup
objectClass: top
cn: ldapuser
userPassword: {crypt}x
gidNumber: 506
Now we will add this ldif file too to ldap database, similarly as we did for base.ldif file as below .
[root@server1 migration]# ldapadd -x -D "cn=admin,dc=shirishlinux,dc=com" -W -f /root/LDAP/ldapuser_u.ldif
Enter LDAP Password:
adding new entry "uid=ldapuser,ou=People,dc=shirishlinux,dc=com"
[root@server1 migration]# ldapadd -x -D "cn=admin,dc=shirishlinux,dc=com" -W -f /root/LDAP/ldapuser_g.ldif
Enter LDAP Password:
adding new entry "cn=ldapuser,ou=Group,dc=shirishlinux,dc=com"
[root@server1 migration]#
Now will verify our above entry in ldap database using ldapsearch command
[root@server1 migration]# ldapsearch -x -b 'dc=shirishlinux,dc=com' '(cn=ldapuser)'
# extended LDIF
#
# LDAPv3
# base <dc=shirishlinux,dc=com> with scope subtree
# filter: (cn=ldapuser)
# requesting: ALL
#
# ldapuser, People, shirishlinux.com
dn: uid=ldapuser,ou=People,dc=shirishlinux,dc=com
uid: ldapuser
cn: ldapuser
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:: e2NyeXB0fSQxJER4c1Fib09XJG01NmNPLjFlL0xET2FXem5IRDNsbC8=
shadowLastChange: 15968
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 505
gidNumber: 506
homeDirectory: /home/ldapuser
# ldapuser, Group, shirishlinux.com
dn: cn=ldapuser,ou=Group,dc=shirishlinux,dc=com
objectClass: posixGroup
objectClass: top
cn: ldapuser
userPassword:: e2NyeXB0fXg=
gidNumber: 506
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2
[root@server1 migration]#
Now we have done with ldap server end.. now at client server: client.shirish.com
Note: here am doing each communication via IP address, you can do using either ip/hostname which you prefer, but ensure hostname is getting resolve by your DNS server or have proper entry in /etc/hosts file .
Now will configure client server for the login authentication from our ldap server : server.shirish.com(192.168.8.10)
Install required packages using yum .
CLI way: manually add/modify /etc/ldap.conf with below entries
base dc=shirishlinux,dc=com
uri ldap://192.168.8.10/
Add/Modify /etc/nsswitch.conf with below entries
passwd: files ldap
shadow: files ldap
group: files ldap
netgroup: nisplus ldap
GUI_WAY: Run authconfig-tui from CLI as below .
[root@client ~]# authconfig-tui
[root@server2 ~]# id ldapuser
uid=505(ldapuser) gid=506(ldapuser) groups=506(ldapuser)
[root@server2 ~]#
Good Congratulation!!! :) now user : ldapuser is logged in on client system.
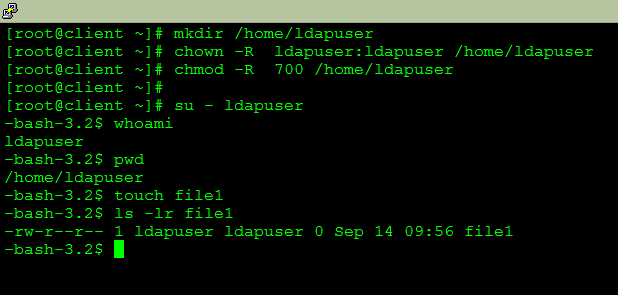
BUT 1. Here user is not able to create any file and does not have any home directory for him .
So we will create home for user and try again login .
Great wow, it works... but ..but .. what if there are 1000 servers and 100 users, it will be tough task for admin to perform such steps for all users on all servers ..
Here below are solutions for same .
1. NFS shared home for each user, which will get auto mounted upon login
2. Upon user login, his home directory and other files get auto created locally on respective servers .
Above I will cover in coming blog .. keep learning .. have a great day .
Today various modes are there to authenticate system devices such as AD(Microsoft active directory) and AAA but LDAP (Light weight directory access protocol) is kind of protocol have it's unique place which use it's own database to authenticate various services applications such as mail, squid, samba, webpages servers and various network devices .
Here we are going to configure ldap server and Linux (centOs 5.7) client for user authentication from LDAP server .
These steps help you to configure Ldap server to act as centralized authentication server for your Linux/Unix servers .
Eg:
Server: server.shirish.com (192.168.8.10)
Client : client.shirish.com (192.168.8.20)
Prerequisite :
1. Proper communication and required ports opens between client and server (default ports : 389 and ssh 22 )
2. Assuming you have proper DNS resolver
3. Yum server configured to install necessary packages .
Do following seps at LDAP server: server.shirish.com end
Steps:1. Installing Openldap on Linux server (ie.LDAP server)
Login to server : server.shirish.com as root and install following packages .
Required Packages to be installed .
openldap
openldap-clients
openldap-devel
openldap-servers
nss_ldap
[root@server1 ~]# yum -y install openldap*
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
Setting up Install Process
Package openldap-2.3.43-12.el5_6.7.i386 already installed and latest version
Resolving Dependencies
--> Running transaction check
---> Package openldap-clients.i386 0:2.3.43-12.el5_6.7 set to be updated
---> Package openldap-devel.i386 0:2.3.43-12.el5_6.7 set to be updated
--> Processing Dependency: cyrus-sasl-devel >= 2.1 for package: openldap-devel
---> Package openldap-servers.i386 0:2.3.43-12.el5_6.7 set to be updated
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
Setting up Install Process
Package openldap-2.3.43-12.el5_6.7.i386 already installed and latest version
Resolving Dependencies
--> Running transaction check
---> Package openldap-clients.i386 0:2.3.43-12.el5_6.7 set to be updated
---> Package openldap-devel.i386 0:2.3.43-12.el5_6.7 set to be updated
--> Processing Dependency: cyrus-sasl-devel >= 2.1 for package: openldap-devel
---> Package openldap-servers.i386 0:2.3.43-12.el5_6.7 set to be updated
.
.
[root@server1 CentOS]# cd /etc/openldap/
[root@server1 openldap]# pwd
/etc/openldap
[root@server1 openldap]#
[root@server1 openldap]# ls -lrt
total 28
-rw-r----- 1 root ldap 921 Mar 31 2011 DB_CONFIG.example
-rw-r----- 1 root ldap 3799 Mar 31 2011 slapd.conf
-rw-r--r-- 1 root root 246 Mar 31 2011 ldap.conf
drwxr-xr-x 2 root root 4096 Mar 31 2011 cacerts
drwxr-xr-x 3 root root 4096 Aug 17 12:05 schema
[root@server1 openldap]#
[root@server1 openldap]# pwd
/etc/openldap
[root@server1 openldap]#
[root@server1 openldap]# ls -lrt
total 28
-rw-r----- 1 root ldap 921 Mar 31 2011 DB_CONFIG.example
-rw-r----- 1 root ldap 3799 Mar 31 2011 slapd.conf
-rw-r--r-- 1 root root 246 Mar 31 2011 ldap.conf
drwxr-xr-x 2 root root 4096 Mar 31 2011 cacerts
drwxr-xr-x 3 root root 4096 Aug 17 12:05 schema
[root@server1 openldap]#
2. Create Password for LDAP admin
have to copy this encrypted password in slapd.conf file)
[root@server1 openldap]# slappasswd
New password:
Re-enter new password:
{SSHA}p+IMM8pNWzGirnHTizlpc2IwSrc6rgXR
[root@server1 openldap]# slappasswd
New password:
Re-enter new password:
{SSHA}p+IMM8pNWzGirnHTizlpc2IwSrc6rgXR
[root@server1 openldap]#
3.Now add/change following lines in your /etc/openldap/slapd.conf file .
include /etc/openldap/schema/core.schema
include /etc/openldap/schema/cosine.schema
include /etc/openldap/schema/inetorgperson.schema
include /etc/openldap/schema/nis.schema
include /etc/openldap/schema/redhat/autofs.schema
allow bind_v2
pidfile /var/run/openldap/slapd.pid
argsfile /var/run/openldap/slapd.args
database bdb
suffix "dc=shirishlinux,dc=com"
rootdn "cn=admin,dc=shirishlinux,dc=com"
password-hash {CRYPT}
rootpw {SSHA}p+IMM8pNWzGirnHTizlpc2IwSrc6rgXR
directory /var/lib/ldap
index objectClass eq,pres
index ou,cn,mail,surname,givenname eq,pres,sub
index uidNumber,gidNumber,loginShell eq,pres
index uid,memberUid eq,pres,sub
index nisMapName,nisMapEntry eq,pres,sub
Verify above your changes by ..
[root@server1 openldap]# egrep -v "^#|^$" /etc/openldap/slapd.conf
index objectClass eq,pres
index ou,cn,mail,surname,givenname eq,pres,sub
index uidNumber,gidNumber,loginShell eq,pres
index uid,memberUid eq,pres,sub
index nisMapName,nisMapEntry eq,pres,sub
Verify above your changes by ..
[root@server1 openldap]# egrep -v "^#|^$" /etc/openldap/slapd.conf
3. Now copy /etc/openldap/DB_CONFIG.example file to /var/lib/ldap/DB_CONFIG directory
[root@server1 openldap]# cd /etc/openldap/
[root@server1 openldap]# cp -rp DB_CONFIG.example /var/lib/ldap/DB_CONFIG
[root@server1 openldap]# ls -ld /var/lib/ldap/ <-- Make sure your ldap directory permission .
drwx------ 2 ldap ldap 4096 Aug 17 12:22 /var/lib/ldap/
[root@server1 openldap]# ls -ld /var/lib/ldap/DB_CONFIG
-rw-r----- 1 root ldap 921 Mar 31 2011 /var/lib/ldap/DB_CONFIG
[root@server1 openldap]#
[root@server1 openldap]# chown ldap:ldap /var/lib/ldap/DB_CONFIG
[root@server1 openldap]# chmod 600 /var/lib/ldap/DB_CONFIG
[root@server1 openldap]# ls -ld /var/lib/ldap/ <-- Make sure your ldap directory permission .
drwx------ 2 ldap ldap 4096 Aug 17 12:22 /var/lib/ldap/
[root@server1 openldap]# ls -ld /var/lib/ldap/DB_CONFIG
-rw-r----- 1 root ldap 921 Mar 31 2011 /var/lib/ldap/DB_CONFIG
[root@server1 openldap]#
[root@server1 openldap]# chown ldap:ldap /var/lib/ldap/DB_CONFIG
[root@server1 openldap]# chmod 600 /var/lib/ldap/DB_CONFIG
Now start ldap service
[root@server1 openldap]# /etc/init.d/ldap start
Checking configuration files for slapd: config file testing succeeded
[ OK ]
Starting slapd: [ OK ]
[root@server1 openldap]#
Checking configuration files for slapd: config file testing succeeded
[ OK ]
Starting slapd: [ OK ]
[root@server1 openldap]#
Now we have to create base schema to understand our domain communicate input and request t ldap server .
There are various way to create it, but easiest way which admin prefer is migrate scripts available at path "/usr/share/openldap/migration"
[root@server1 openldap]# cd /usr/share/openldap/migration
[root@server1 migration]# ls -rlt migrate_common.ph
-rw-r--r-- 1 root root 8880 Mar 31 2011 migrate_common.ph
[root@server1 migration]# ls -rlt migrate_common.ph
-rw-r--r-- 1 root root 8880 Mar 31 2011 migrate_common.ph
Take backup of this script .
[root@server1 migration]# cp -rp migrate_common.ph migrate_common.ph_back
This script is made for domain "padl.com" which now we have to change for our "shirishlinux.com" domain as below before running this script .
[root@server1 migration]# grep -i padl migrate_common.ph
$DEFAULT_MAIL_DOMAIN = "padl.com";
$DEFAULT_BASE = "dc=padl,dc=com";
#define(`confLDAP_DEFAULT_SPEC',`-h "ldap.padl.com"')dnl
# $DEFAULT_MAIL_HOST = "mail.padl.com";
[root@server1 migration]#
We will do this changes by sed, but you can do by opening file via "vi" editor too .
First check :
[root@server1 migration]# sed "s/padl/shirishlinux/g" migrate_common.ph | grep -i shirish
$DEFAULT_MAIL_DOMAIN = "shirishlinux.com";
$DEFAULT_BASE = "dc=shirishlinux,dc=com";
#define(`confLDAP_DEFAULT_SPEC',`-h "ldap.shirishlinux.com"')dnl
# $DEFAULT_MAIL_HOST = "mail.shirishlinux.com";
[root@server1 migration]#
Above seems okay, now will implement changes using sed as below .
[root@server1 migration]# sed -i "s/padl/shirishlinux/g" migrate_common.ph
Verify Now ....
[root@server1 migration]# grep -i shirishlinux migrate_common.ph
$DEFAULT_MAIL_DOMAIN = "shirishlinux.com";
$DEFAULT_BASE = "dc=shirishlinux,dc=com";
#define(`confLDAP_DEFAULT_SPEC',`-h "ldap.shirishlinux.com"')dnl
# $DEFAULT_MAIL_HOST = "mail.shirishlinux.com";
[root@server1 migration]#
The above seems fine, as per our requirement .
Now we will create structure base schema for ldap database using this script as below .
[root@server1 migration]# mkdir /root/LDAP
[root@server1 migration]# ./migrate_base.pl > /root/LDAP/base.ldif
Now just look ad base.ldif schema file, will get bit idea about it by looking at various fields of this .
[root@server1 migration]# cat /root/LDAP/base.ldif
dn: dc=shirishlinux,dc=com
dc: shirishlinux
objectClass: top
objectClass: domain
dn: ou=Hosts,dc=shirishlinux,dc=com
ou: Hosts
objectClass: top
objectClass: organizationalUnit
dn: ou=Rpc,dc=shirishlinux,dc=com
ou: Rpc
objectClass: top
objectClass: organizationalUnit
dn: ou=Services,dc=shirishlinux,dc=com
ou: Services
objectClass: top
objectClass: organizationalUnit
dn: nisMapName=netgroup.byuser,dc=shirishlinux,dc=com
nismapname: netgroup.byuser
objectClass: top
objectClass: nisMap
dn: ou=Mounts,dc=shirishlinux,dc=com
ou: Mounts
objectClass: top
objectClass: organizationalUnit
dn: ou=Networks,dc=shirishlinux,dc=com
ou: Networks
objectClass: top
objectClass: organizationalUnit
dn: ou=People,dc=shirishlinux,dc=com
ou: People
objectClass: top
objectClass: organizationalUnit
dn: ou=Group,dc=shirishlinux,dc=com
ou: Group
objectClass: top
objectClass: organizationalUnit
dn: ou=Netgroup,dc=shirishlinux,dc=com
ou: Netgroup
objectClass: top
objectClass: organizationalUnit
dn: ou=Protocols,dc=shirishlinux,dc=com
ou: Protocols
objectClass: top
objectClass: organizationalUnit
dn: ou=Aliases,dc=shirishlinux,dc=com
ou: Aliases
objectClass: top
objectClass: organizationalUnit
dn: nisMapName=netgroup.byhost,dc=shirishlinux,dc=com
nismapname: netgroup.byhost
objectClass: top
objectClass: nisMap
Now we will add this ldif file to LDAP database by using ldapadd command .
Here..
-X Authzid SASL authorization identity ("dn:<dn>" or "u:<user>")
-x Simple authentication
-W Prompt for bind password
-D Binddn bind DN
-f File read operations from `file'
[root@server1 migration]# ldapadd -x -D "cn=admin,dc=shirishlinux,dc=com" -W -f /root/LDAP/base.ldif
Enter LDAP Password:
adding new entry "dc=shirishlinux,dc=com"
adding new entry "ou=Hosts,dc=shirishlinux,dc=com"
adding new entry "ou=Rpc,dc=shirishlinux,dc=com"
adding new entry "ou=Services,dc=shirishlinux,dc=com"
adding new entry "nisMapName=netgroup.byuser,dc=shirishlinux,dc=com"
adding new entry "ou=Mounts,dc=shirishlinux,dc=com"
adding new entry "ou=Networks,dc=shirishlinux,dc=com"
adding new entry "ou=People,dc=shirishlinux,dc=com"
adding new entry "ou=Group,dc=shirishlinux,dc=com"
adding new entry "ou=Netgroup,dc=shirishlinux,dc=com"
adding new entry "ou=Protocols,dc=shirishlinux,dc=com"
adding new entry "ou=Aliases,dc=shirishlinux,dc=com"
adding new entry "nisMapName=netgroup.byhost,dc=shirishlinux,dc=com"
[root@server1 migration]#
Now it's time to create user and add same in ldap database .
1. Create a normal user on ldap server say ldapuser
[root@server1 migration]# useradd ldapuser
[root@server1 migration]# passwd ldapuser
Changing password for user ldapuser.
New UNIX password:
BAD PASSWORD: it is WAY too short
Retype new UNIX password:
passwd: all authentication tokens updated successfully.
[root@server1 migration]#
[root@server1 migration]# getent passwd ldapuser
ldapuser:x:505:506::/home/ldapuser:/bin/bash
[root@server1 migration]#
/usr/share/openldap/migration/migrate_passwd.pl [root@server1 migration]# grep -i ldapuser /etc/passwdldapuser:x:505:506::/home/ldapuser:/bin/bash
[root@server1 migration]#
[root@server1 migration]# grep -i ldapuser /etc/passwd > /root/LDAP/ldapuser_u
Note: Here we are using default home for user, but problem is when user with same name exit's on client server, so it's better to avoid such situation .
Later in this blog will see how to export NFS home directory for each user, which get's auto mounted upon user login .
Now migrate this ldif file with migration script"
/usr/share/openldap/migration/migrate_passwd.pl" as below .
[root@server1 migration]# /usr/share/openldap/migration/migrate_passwd.pl /root/LDAP/ldapuser_u /root/LDAP/ldapuser_u.ldif
[root@server1 migration]#
[root@server1 migration]# cat /root/LDAP/ldapuser_u.ldif
dn: uid=ldapuser,ou=People,dc=shirishlinux,dc=com
uid: ldapuser
cn: ldapuser
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: {crypt}$1$DxsQboOW$m56cO.1e/LDOaWznHD3ll/
shadowLastChange: 15968
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 505
gidNumber: 506
homeDirectory: /home/ldapuser
[root@server1 migration]#
dn: dc=shirishlinux,dc=com
dc: shirishlinux
objectClass: top
objectClass: domain
dn: ou=Hosts,dc=shirishlinux,dc=com
ou: Hosts
objectClass: top
objectClass: organizationalUnit
dn: ou=Rpc,dc=shirishlinux,dc=com
ou: Rpc
objectClass: top
objectClass: organizationalUnit
dn: ou=Services,dc=shirishlinux,dc=com
ou: Services
objectClass: top
objectClass: organizationalUnit
dn: nisMapName=netgroup.byuser,dc=shirishlinux,dc=com
nismapname: netgroup.byuser
objectClass: top
objectClass: nisMap
dn: ou=Mounts,dc=shirishlinux,dc=com
ou: Mounts
objectClass: top
objectClass: organizationalUnit
dn: ou=Networks,dc=shirishlinux,dc=com
ou: Networks
objectClass: top
objectClass: organizationalUnit
dn: ou=People,dc=shirishlinux,dc=com
ou: People
objectClass: top
objectClass: organizationalUnit
dn: ou=Group,dc=shirishlinux,dc=com
ou: Group
objectClass: top
objectClass: organizationalUnit
dn: ou=Netgroup,dc=shirishlinux,dc=com
ou: Netgroup
objectClass: top
objectClass: organizationalUnit
dn: ou=Protocols,dc=shirishlinux,dc=com
ou: Protocols
objectClass: top
objectClass: organizationalUnit
dn: ou=Aliases,dc=shirishlinux,dc=com
ou: Aliases
objectClass: top
objectClass: organizationalUnit
dn: nisMapName=netgroup.byhost,dc=shirishlinux,dc=com
nismapname: netgroup.byhost
objectClass: top
objectClass: nisMap
Now we will add this ldif file to LDAP database by using ldapadd command .
Here..
-X Authzid SASL authorization identity ("dn:<dn>" or "u:<user>")
-x Simple authentication
-W Prompt for bind password
-D Binddn bind DN
-f File read operations from `file'
[root@server1 migration]# ldapadd -x -D "cn=admin,dc=shirishlinux,dc=com" -W -f /root/LDAP/base.ldif
Enter LDAP Password:
adding new entry "dc=shirishlinux,dc=com"
adding new entry "ou=Hosts,dc=shirishlinux,dc=com"
adding new entry "ou=Rpc,dc=shirishlinux,dc=com"
adding new entry "ou=Services,dc=shirishlinux,dc=com"
adding new entry "nisMapName=netgroup.byuser,dc=shirishlinux,dc=com"
adding new entry "ou=Mounts,dc=shirishlinux,dc=com"
adding new entry "ou=Networks,dc=shirishlinux,dc=com"
adding new entry "ou=People,dc=shirishlinux,dc=com"
adding new entry "ou=Group,dc=shirishlinux,dc=com"
adding new entry "ou=Netgroup,dc=shirishlinux,dc=com"
adding new entry "ou=Protocols,dc=shirishlinux,dc=com"
adding new entry "ou=Aliases,dc=shirishlinux,dc=com"
adding new entry "nisMapName=netgroup.byhost,dc=shirishlinux,dc=com"
[root@server1 migration]#
Now it's time to create user and add same in ldap database .
1. Create a normal user on ldap server say ldapuser
[root@server1 migration]# useradd ldapuser
[root@server1 migration]# passwd ldapuser
Changing password for user ldapuser.
New UNIX password:
BAD PASSWORD: it is WAY too short
Retype new UNIX password:
passwd: all authentication tokens updated successfully.
[root@server1 migration]#
[root@server1 migration]# getent passwd ldapuser
ldapuser:x:505:506::/home/ldapuser:/bin/bash
[root@server1 migration]#
/usr/share/openldap/migration/migrate_passwd.pl [root@server1 migration]# grep -i ldapuser /etc/passwdldapuser:x:505:506::/home/ldapuser:/bin/bash
[root@server1 migration]#
[root@server1 migration]# grep -i ldapuser /etc/passwd > /root/LDAP/ldapuser_u
Note: Here we are using default home for user, but problem is when user with same name exit's on client server, so it's better to avoid such situation .
Later in this blog will see how to export NFS home directory for each user, which get's auto mounted upon user login .
Now migrate this ldif file with migration script"
/usr/share/openldap/migration/migrate_passwd.pl" as below .
[root@server1 migration]# /usr/share/openldap/migration/migrate_passwd.pl /root/LDAP/ldapuser_u /root/LDAP/ldapuser_u.ldif
[root@server1 migration]#
[root@server1 migration]# cat /root/LDAP/ldapuser_u.ldif
dn: uid=ldapuser,ou=People,dc=shirishlinux,dc=com
uid: ldapuser
cn: ldapuser
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: {crypt}$1$DxsQboOW$m56cO.1e/LDOaWznHD3ll/
shadowLastChange: 15968
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 505
gidNumber: 506
homeDirectory: /home/ldapuser
[root@server1 migration]#
Similarly we will do for group file entry as below of the user "ldapuser"
[root@server1 migration]# grep -i ldapuser /etc/group > /root/LDAP/ldapuser_g
[root@server1 migration]# cat /root/LDAP/ldapuser_g
ldapuser:x:506:
[root@server1 migration]#
[root@server1 migration]# /usr/share/openldap/migration/migrate_group.pl /root/LDAP/ldapuser_g /root/LDAP/ldapuser_g.ldif
[root@server1 migration]#
[root@server1 migration]# cat /root/LDAP/ldapuser_g.ldif
dn: cn=ldapuser,ou=Group,dc=shirishlinux,dc=com
objectClass: posixGroup
objectClass: top
cn: ldapuser
userPassword: {crypt}x
gidNumber: 506
Now we will add this ldif file too to ldap database, similarly as we did for base.ldif file as below .
[root@server1 migration]# ldapadd -x -D "cn=admin,dc=shirishlinux,dc=com" -W -f /root/LDAP/ldapuser_u.ldif
Enter LDAP Password:
adding new entry "uid=ldapuser,ou=People,dc=shirishlinux,dc=com"
[root@server1 migration]# ldapadd -x -D "cn=admin,dc=shirishlinux,dc=com" -W -f /root/LDAP/ldapuser_g.ldif
Enter LDAP Password:
adding new entry "cn=ldapuser,ou=Group,dc=shirishlinux,dc=com"
[root@server1 migration]#
Now will verify our above entry in ldap database using ldapsearch command
[root@server1 migration]# ldapsearch -x -b 'dc=shirishlinux,dc=com' '(cn=ldapuser)'
# extended LDIF
#
# LDAPv3
# base <dc=shirishlinux,dc=com> with scope subtree
# filter: (cn=ldapuser)
# requesting: ALL
#
# ldapuser, People, shirishlinux.com
dn: uid=ldapuser,ou=People,dc=shirishlinux,dc=com
uid: ldapuser
cn: ldapuser
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword:: e2NyeXB0fSQxJER4c1Fib09XJG01NmNPLjFlL0xET2FXem5IRDNsbC8=
shadowLastChange: 15968
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 505
gidNumber: 506
homeDirectory: /home/ldapuser
# ldapuser, Group, shirishlinux.com
dn: cn=ldapuser,ou=Group,dc=shirishlinux,dc=com
objectClass: posixGroup
objectClass: top
cn: ldapuser
userPassword:: e2NyeXB0fXg=
gidNumber: 506
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2
[root@server1 migration]#
Now we have done with ldap server end.. now at client server: client.shirish.com
Note: here am doing each communication via IP address, you can do using either ip/hostname which you prefer, but ensure hostname is getting resolve by your DNS server or have proper entry in /etc/hosts file .
Now will configure client server for the login authentication from our ldap server : server.shirish.com(192.168.8.10)
Install required packages using yum .
[root@server2 ~]# yum -y install openldap openldap-clients openldap-devel nss_ldap
CLI way: manually add/modify /etc/ldap.conf with below entries
base dc=shirishlinux,dc=com
uri ldap://192.168.8.10/
Add/Modify /etc/nsswitch.conf with below entries
passwd: files ldap
shadow: files ldap
group: files ldap
netgroup: nisplus ldap
GUI_WAY: Run authconfig-tui from CLI as below .
[root@client ~]# authconfig-tui
[root@server2 ~]# id ldapuser
uid=505(ldapuser) gid=506(ldapuser) groups=506(ldapuser)
[root@server2 ~]#
Good Congratulation!!! :) now user : ldapuser is logged in on client system.
BUT 1. Here user is not able to create any file and does not have any home directory for him .
So we will create home for user and try again login .
Great wow, it works... but ..but .. what if there are 1000 servers and 100 users, it will be tough task for admin to perform such steps for all users on all servers ..
Here below are solutions for same .
1. NFS shared home for each user, which will get auto mounted upon login
2. Upon user login, his home directory and other files get auto created locally on respective servers .